Introduction
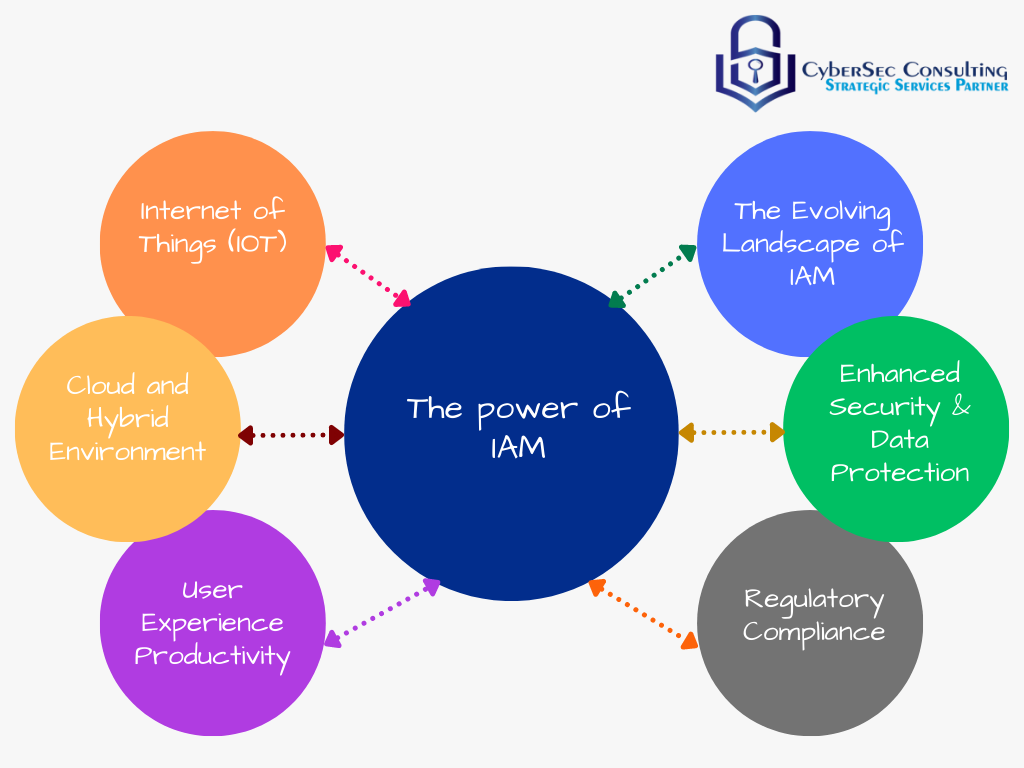
In today’s digital landscape, where data breaches and cyber threats are rampant, securing sensitive information and controlling access to resources have become paramount for organizations of all sizes. Traditional Identity and Access Management (IAM) systems, while effective, are often complex to manage and struggle to keep pace with the dynamic nature of modern IT environments. Enter cloud-based IAM solutions – a game-changer in the realm of cybersecurity. This comprehensive guide aims to explore the intricacies of cloud-based IAM, highlighting its benefits, core components, implementation strategies, and future trends.
Understanding Cloud-based IAM
Cloud-based IAM represents a paradigm shift from on-premises IAM systems to scalable, flexible, and cost-effective solutions hosted in the cloud. At its core, cloud-based IAM encompasses a suite of tools and services designed to manage user identities, control access to resources, and enforce security policies across cloud and hybrid environments. Unlike traditional IAM solutions, which often require significant upfront investment in hardware and infrastructure, cloud-based IAM offers a subscription-based model, allowing organizations to pay only for what they use.
The Need for Cloud-based IAM
The shift to cloud-based IAM is driven by several factors, including the limitations of traditional IAM systems, the growing complexity of IT infrastructures, and the need for enhanced security and compliance measures. Traditional IAM solutions often struggle to scale to meet the demands of modern cloud environments, leading to operational inefficiencies and increased security risks. Additionally, regulatory requirements such as GDPR and CCPA mandate strict data protection measures, further incentivizing organizations to adopt cloud-based IAM solutions that offer robust security features and compliance controls.
Core Components of Cloud-based IAM Solutions
Cloud-based IAM solutions typically consist of several core components, each serving a specific function in the identity and access management lifecycle. These components include:
- User Provisioning and Deprovisioning: Automates the process of creating, modifying, and deleting user accounts and access rights based on predefined policies and workflows.
- Single Sign-On (SSO): Allows users to authenticate once and access multiple applications and services without the need to re-enter their credentials.
- Multi-factor Authentication (MFA): Enhances security by requiring users to provide multiple forms of verification, such as passwords, biometrics, or one-time codes, before granting access.
- Role-based Access Control (RBAC): Assigns permissions to users based on their roles and responsibilities within the organization, ensuring that they only have access to the resources necessary to perform their job functions.
- Audit Logs and Reporting Functionalities: Provides visibility into user activities, access requests, and policy violations through comprehensive audit logs and reporting tools.
Advantages of Cloud-based IAM Solutions
The adoption of cloud-based IAM offers several significant advantages for organizations seeking to improve their security posture and streamline access management processes:
- Enhanced Security: Cloud-based IAM solutions leverage advanced security features such as encryption, threat detection, and anomaly detection to protect against unauthorized access and data breaches.
- Improved User Experience: SSO capabilities enable users to access multiple applications and services with a single set of credentials, enhancing productivity and reducing password fatigue.
- Cost-effectiveness: Cloud-based IAM solutions eliminate the need for upfront investment in hardware and infrastructure, allowing organizations to pay only for the resources they consume on a subscription basis.
- Scalability: Cloud-based IAM solutions can easily scale to accommodate growing user populations and evolving business requirements, ensuring that organizations can adapt to changing needs without compromising security or performance.
- Seamless Integration: Cloud-based IAM solutions seamlessly integrate with a wide range of cloud applications and services, enabling organizations to centralize access management and enforce consistent security policies across their entire IT environment.
Implementing Cloud-based IAM
Successfully implementing a cloud-based IAM solution requires careful planning, thorough assessment of organizational needs, and effective collaboration between IT teams and stakeholders. The following steps can help guide organizations through the implementation process:
- Assessment of Organizational Needs and Requirements: Conduct a comprehensive assessment of current IAM practices, identify key pain points and areas for improvement, and define clear objectives and success criteria for the cloud-based IAM implementation.
- Vendor Selection and Evaluation Criteria: Evaluate potential vendors based on factors such as product features, scalability, security, reliability, and vendor reputation. Consider conducting proof-of-concept trials or requesting demos to assess the suitability of the solution for your organization’s specific needs.
- Planning and Deployment Strategies: Develop a detailed implementation plan outlining key milestones, timelines, and resource requirements. Consider leveraging phased deployment approaches to minimize disruption to business operations and facilitate smooth transition to the new IAM solution.
- Integration with Existing Systems and Applications: Ensure seamless integration with existing IT systems, applications, and directories to facilitate user provisioning, authentication, and access control processes. Consider leveraging standard protocols such as SAML, OAuth, and LDAP for interoperability and compatibility with third-party solutions.
Case Studies and Examples
Real-world examples of organizations benefiting from cloud-based IAM solutions:
- Company X: By migrating to a cloud-based IAM solution, Company X was able to streamline access management processes, reduce administrative overhead, and improve security posture across its global workforce.
- Company Y: Company Y implemented a cloud-based IAM solution to meet stringent regulatory requirements and enhance data protection measures. The solution provided comprehensive audit trails and reporting functionalities, enabling Company Y to demonstrate compliance with industry regulations and standards.
Best Practices for Cloud-based IAM
To maximize the effectiveness of cloud-based IAM solutions, organizations should adhere to the following best practices:
- Regular Audits and Updates of Access Policies: Conduct regular audits of user access rights and permissions to identify and remediate any unauthorized or excessive privileges. Implement automated workflows for provisioning and deprovisioning user accounts to ensure timely removal of access for employees who leave the organization or change roles.
- Employee Training and Awareness Programs: Educate employees about the importance of security best practices, such as creating strong passwords, safeguarding sensitive information, and recognizing phishing attempts. Provide ongoing training and awareness programs to reinforce security awareness and promote a culture of security within the organization.
- Continuous Monitoring and Threat Detection: Implement robust monitoring and logging mechanisms to detect and respond to security incidents in real-time. Leverage advanced analytics and machine learning techniques to identify anomalous behavior patterns and potential security threats, enabling proactive threat mitigation and incident response.
- Collaboration with Trusted Partners and Vendors: Collaborate with trusted partners and vendors to leverage their expertise and resources in implementing and managing cloud-based IAM solutions. Establish clear lines of communication and accountability to ensure effective collaboration and alignment with organizational goals and objectives.
Future Trends in Cloud-based IAM
The future of cloud-based IAM is ripe with innovation and advancements, driven by emerging technologies and evolving security threats. Some key trends to watch out for include:
- Evolution of IAM Technologies and Standards: IAM solutions will continue to evolve to address emerging security threats and regulatory requirements. Expect to see advancements in areas such as biometric authentication, identity federation, and identity-as-a-service (IDaaS) offerings.
- Adoption of Artificial Intelligence (AI) and Machine Learning (ML): AI and ML technologies will play an increasingly important role in enhancing the security and usability of IAM solutions. These technologies can help organizations automate routine tasks, detect and respond to security threats in real-time, and provide personalized user experiences.
- Impact of Internet of Things (IoT) and Edge Computing: The proliferation of IoT devices and edge computing environments will pose new challenges for IAM solutions. Organizations will need to implement IAM controls to securely manage access to IoT devices, applications, and data, while ensuring compliance with regulatory requirements and industry standards.
Conclusion
Cloud-based IAM solutions offer a compelling value proposition for organizations seeking to enhance their security posture, streamline access management processes, and meet compliance requirements. By leveraging advanced security features, scalability, and seamless integration capabilities, organizations can effectively manage user identities, control access to resources, and enforce security policies across cloud and hybrid environments. As the threat landscape continues to evolve, organizations must remain vigilant and proactive in adopting cloud-based IAM solutions to safeguard their sensitive information and mitigate security risks. With careful planning, effective implementation strategies, and adherence to best practices, organizations can maximize the benefits of cloud-based IAM solutions and stay ahead of the curve in today’s rapidly changing cybersecurity landscape.